Set attacking and target virtual machine to bridged adapter, get both VM’s ip address
Right VM = Attacker
Left VM = Target
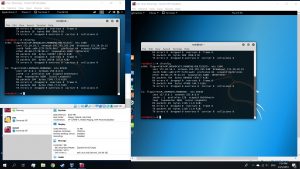
Use command #setoolkit on attacking VM’s terminal. Then follow the options
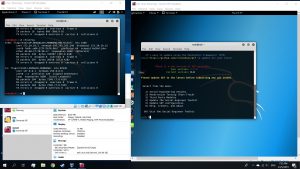
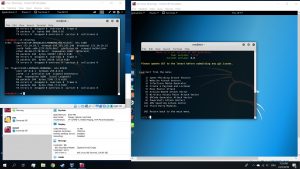
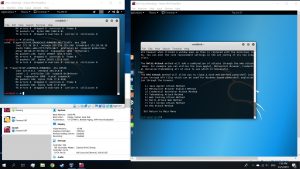
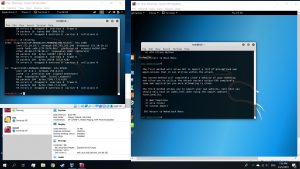
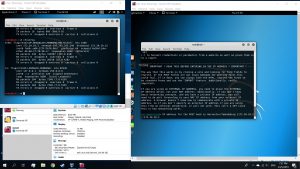
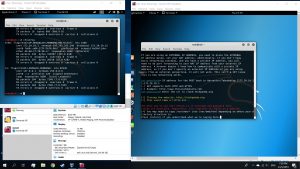
Then, use the commands below on a new tab
#echo 1 > proc/sys/net/ipv4/ip_forward
#arpspoof -t [Target IP] [DNS address]
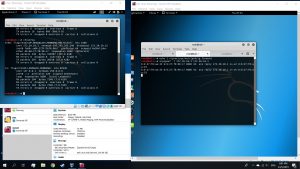
#arpspoof -t [DNS address] [Target IP}
On a new tab
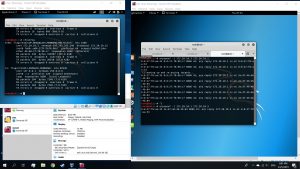
Open a new terminal and use the command
#leafpad /etc/ettercap/etter.conf
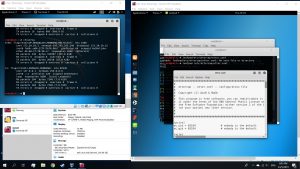
Use find in Search option and search for “Linux”
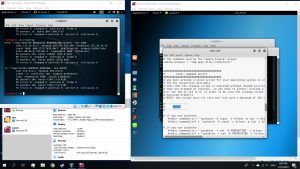
Below the “if you use iptables” part, delete both # (for us to activate the iptables)
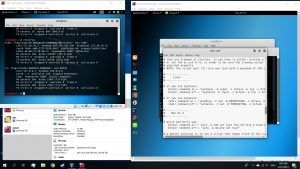
After that, save the file and close it. Use the command
#leafpad /etc/ettercap/etter.dns
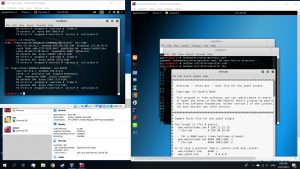
Change the multiple “microsoft.com” lines to the website that is being cloned and change the ip address to your attacking machine’s ip address.
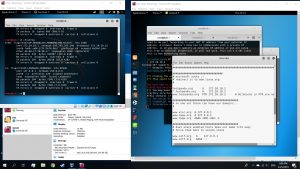
Save the file, and close it. Use the command
#ettercap -G
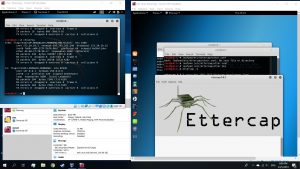
Choose the option sniff, select unified sniffing, click ok with the interface eth0
Select Targets and then current targets
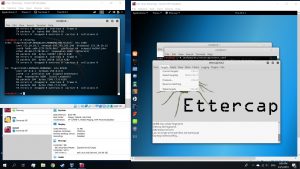
Enter Target’s ip address in Target 1 and DNS address in Target 2
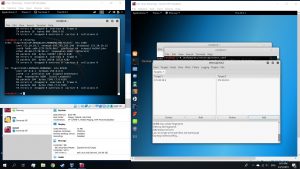
In MITM options, select ARP poisoning and choose sniff remote connections
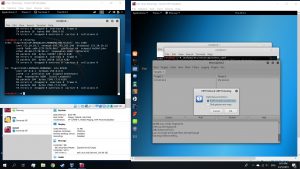
Under plugins tab, choose Manage the Plugins and choose the dns_spoof
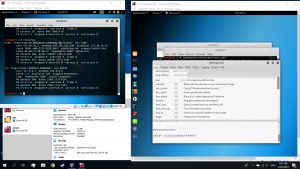
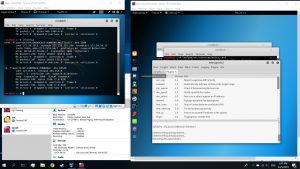
When you ping the website that you cloned in your target’s VM, the ip address that appeared would be the ip address of your attacking VM
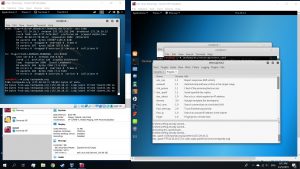
By using the Target browser to enter the website that is cloned, you can get the same exact website as the original one
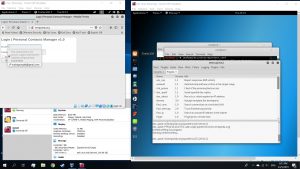
When a username or password is entered, the attacking machine would get a message on the email and password that was inputted
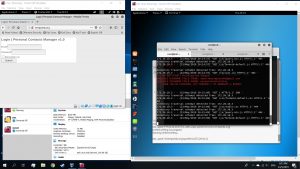
To stop, go to ettercap and stop sniffing

Recent Comments